Thursday 12 November 2015
Hardware End of Life Announcement - SRX100, SRX210, SRX240 and SRX650
End of Life for the SRX-series products listed in the attached document.
This EOL announcement is effective immediately with a Last Order Date
(LOD) of May 1, 2016. On the last order date, the products are removed
from the pricelist and are no longer orderable.
Tuesday 10 November 2015
How to Configure SRX Security Zones with Junos
You cannot manage the SRX Services Gateway as you would a router. The
SRX is a locked-down device. You can’t even ping an interface on the SRX
initially, even if it has a valid IP address. The SRX uses the concept
of nested security zones. Zones are a critical concept in SRX
configuration. No traffic goes in or out unless the security zones are
configured properly on the SRX interfaces.
To configure a security zone, you need to associate the interface with a security zone, and then the security zones need to be bound with a routing instance (if there are multiple routing instances).
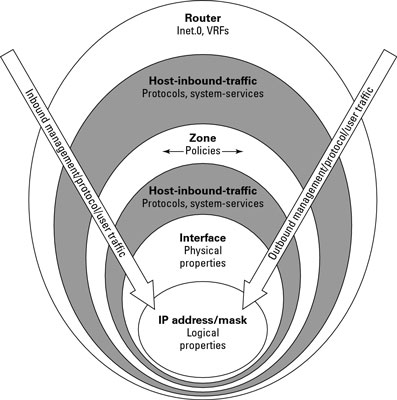 It sounds complicated, but it’s not. First, you configure the zones
and then you associate the interfaces with the zones. Here, we're
assuming that you’re using only one routing instance. You can configure a
zone with more than one interface. However, each interface can belong
to only one zone.
It sounds complicated, but it’s not. First, you configure the zones
and then you associate the interfaces with the zones. Here, we're
assuming that you’re using only one routing instance. You can configure a
zone with more than one interface. However, each interface can belong
to only one zone.
Now, establish two security zones for a simple SRX configuration. One zone is for a local LAN called admins (administration) on interface ge-0/0/0.0, and the other zone is for two links to the Internet called untrust with interfaces ge-0/0/1.0 and ge-0/0/2.0:
This is just an example. Before you enable any services at all on your SRX, make sure you truly need them. FTP in particular is often considered risky because FTP has no real security, and you just punched a big hole for it in your security zone.
Your configuration now looks like this:
To configure a security zone, you need to associate the interface with a security zone, and then the security zones need to be bound with a routing instance (if there are multiple routing instances).
 It sounds complicated, but it’s not. First, you configure the zones
and then you associate the interfaces with the zones. Here, we're
assuming that you’re using only one routing instance. You can configure a
zone with more than one interface. However, each interface can belong
to only one zone.
It sounds complicated, but it’s not. First, you configure the zones
and then you associate the interfaces with the zones. Here, we're
assuming that you’re using only one routing instance. You can configure a
zone with more than one interface. However, each interface can belong
to only one zone.Now, establish two security zones for a simple SRX configuration. One zone is for a local LAN called admins (administration) on interface ge-0/0/0.0, and the other zone is for two links to the Internet called untrust with interfaces ge-0/0/1.0 and ge-0/0/2.0:
root# edit security zones [edit security zones] root# set security zone admins root# set security zone untrust root# set security zone admins interfaces ge-0/0/0.0 root# set security zone untrust interfaces ge-0/0/1.0 root# set security zone untrust interfaces ge-0/0/2.0
Always configure zones from the perspective of the SRX you are configuring. Many other zones may be on the LAN (trust, accounting, and so on). But this SRX only links to admins and untrust.
Now you can add services to the zones you just configured. Assume
that inbound ssh, ftp, and ping traffic is permitted from the untrusted
zone.This is just an example. Before you enable any services at all on your SRX, make sure you truly need them. FTP in particular is often considered risky because FTP has no real security, and you just punched a big hole for it in your security zone.
[edit security zones] root# set security zone untrust host-inbound-traffic ssh root# set security zone untrust host-inbound-traffic ftp root# set security zone untrust host-inbound-traffic ping
Your configuration now looks like this:
[edit security]
zones {
security-zone untrust {
host-inbound-traffic {
system-services {
ssh;
ftp;
ping;
}
}
interfaces {
ge-0/0/1.0;
ge-0/0/2.0;
}
}
security-zone admins {
interfaces {
ge-0/0/0.0;
}
}
Subscribe to:
Posts (Atom)
loading...